Ickie
SOH Administrator
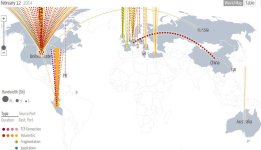
World's largest DDoS strikes US, Europe
http://www.itnews.com.au/News/372033,worlds-largest-ddos-strikes-us-europe.aspx
The power of the vector was demonstrated last month in attacks that took down gaming streaming servers used by professional gamers for EA and League of Legends
“NTP is effective as an amplification source because the responses can be hundreds of times the size of the queries,” Prince explained. “This means that an attacker with a list of a relatively small number of vulnerable NTP servers can generate a large attack. Generally, you only need about 1/10th the number of misconfigured NTP servers as you do open DNS resolvers to launch an attack of the same size.”
http://www.itnews.com.au/News/372033,worlds-largest-ddos-strikes-us-europe.aspx
The power of the vector was demonstrated last month in attacks that took down gaming streaming servers used by professional gamers for EA and League of Legends
“NTP is effective as an amplification source because the responses can be hundreds of times the size of the queries,” Prince explained. “This means that an attacker with a list of a relatively small number of vulnerable NTP servers can generate a large attack. Generally, you only need about 1/10th the number of misconfigured NTP servers as you do open DNS resolvers to launch an attack of the same size.”